Euler hack review
Euler protocol is a lending protocol which allows users to borrow tokens with leverage. It has two tokens: EToken which represents equity and DToken which represents debt.
One of attack transactions:
https://etherscan.io/tx/0xc310a0affe2169d1f6feec1c63dbc7f7c62a887fa48795d327d4d2da2d6b111d
Vulnerability analysis
Since Euler protocol is a lending protocol it has a liquidation process. However, to make liquidation process more efficient, they have introduced Liquidation Discount. In simple words if the position is too unhealthy, liquidators receive up to 20% extra ETokens for liquidating such position.
https://docs.euler.finance/euler-protocol/eulers-default-parameters#maximum-liquidation-discount
Also, if user with bad position doesn’t have enough collateral to satisfy repayment yiled, system will just use the default amount of collateral that user has.
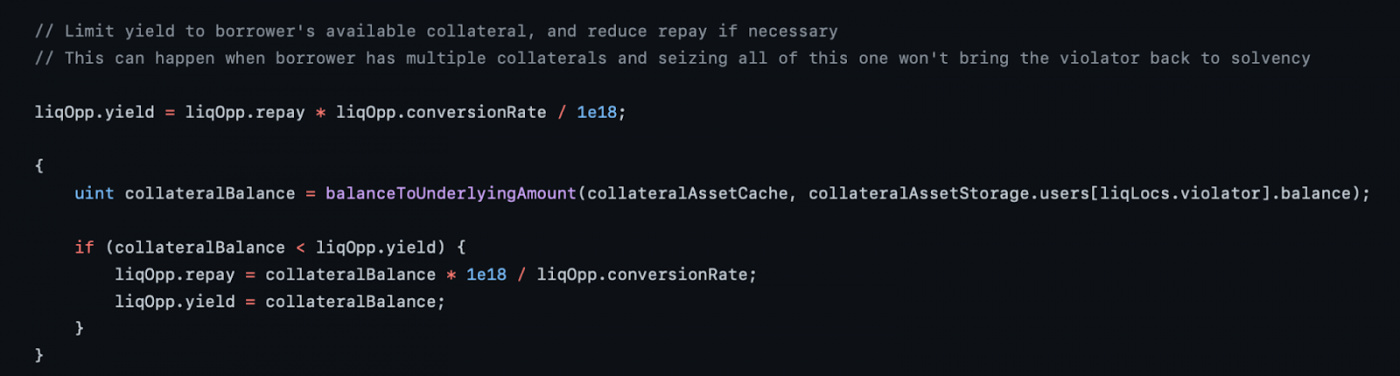
So, what attacker needs to do is to create an undercollateralized position and repay it from another account to get extra discount ETokens.
Creating undercollateralized position is possible due to donateToReserves function in EToken contract.
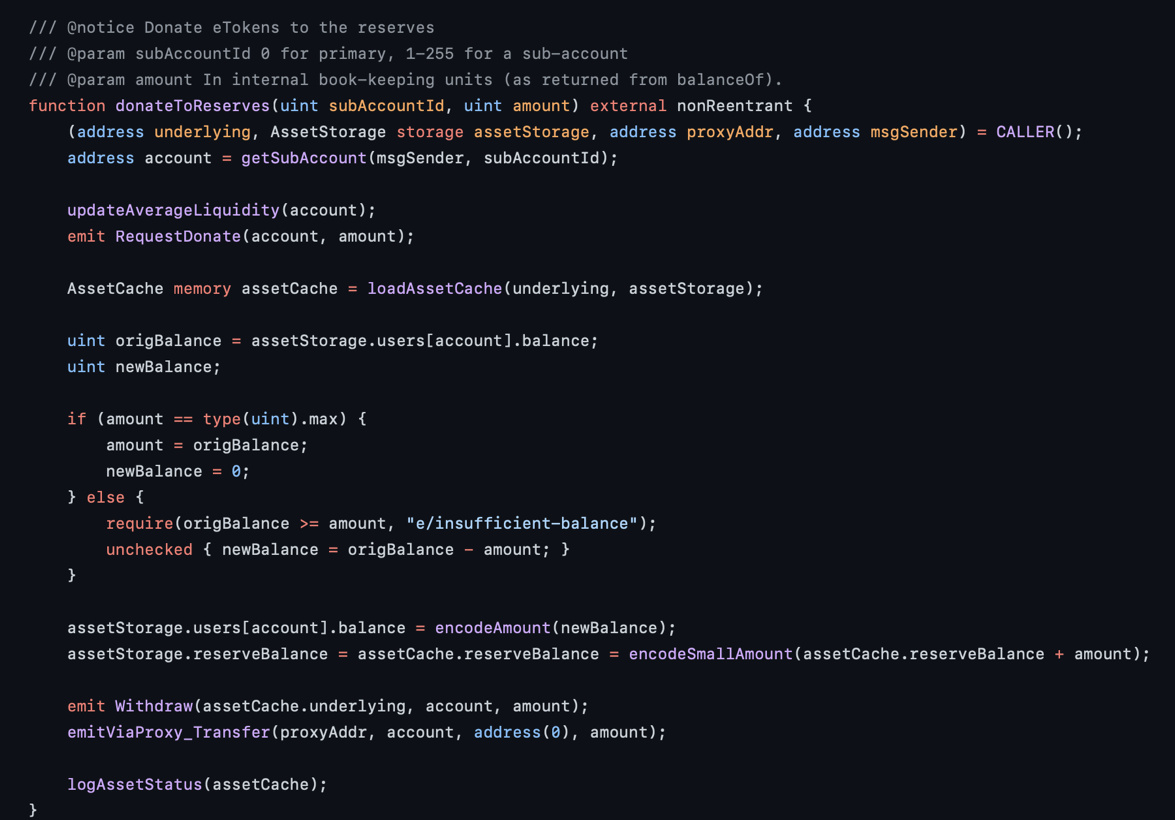
This function allows to donate ETokens to reserves without checking position health status and not affecting user’s DToken’s balance. This results in the reduction of ETokens, when DToken stays unchanged, which immediately makes position undercollateralized.
After that attacker can use another account to liquidate his position with bad debt and gain extra ETokens due to discount.
Attack Flow
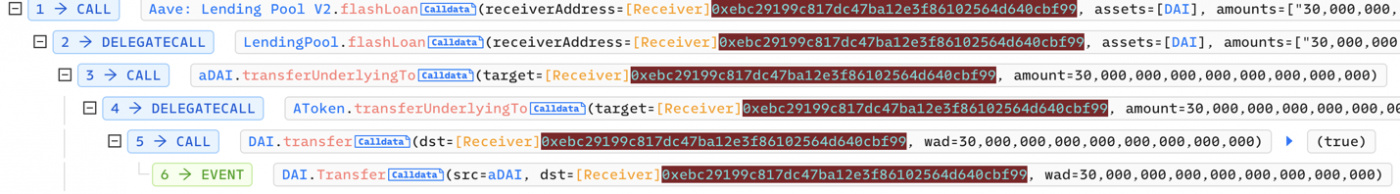
- Attacker takes 30m DAI flashloan from Aave
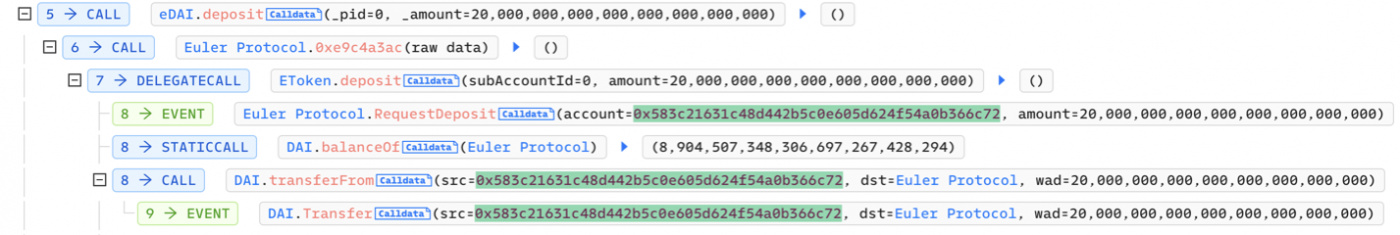
- Attacker deposits 20 mil DAI to Euler Finance and gains about 19.5m eDAI tokens.
- Attacker creates 200m eDAI leverage via minting ~195m eDAI(equity) tokens and ~200m dDAI(debt) tokens.
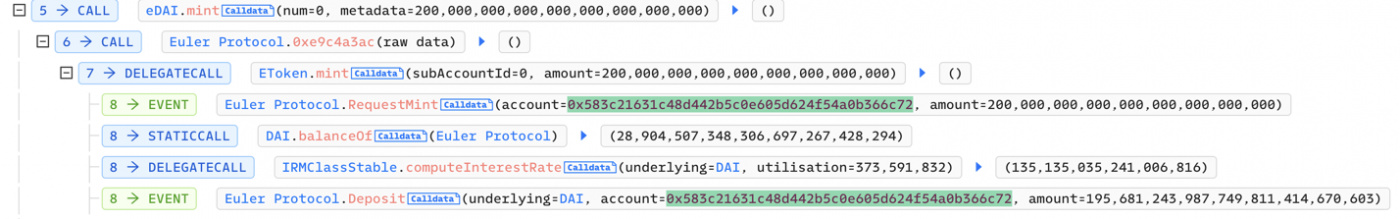
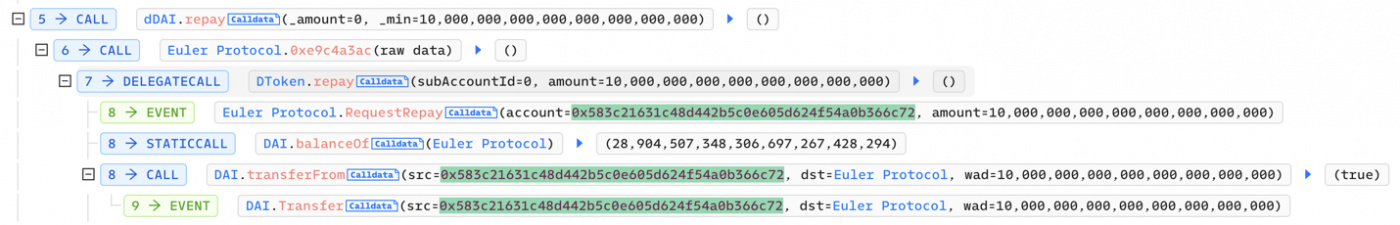
- Attacker repays 10m DAI tokens and lowers his dDAI(debt) tokens to 190m.
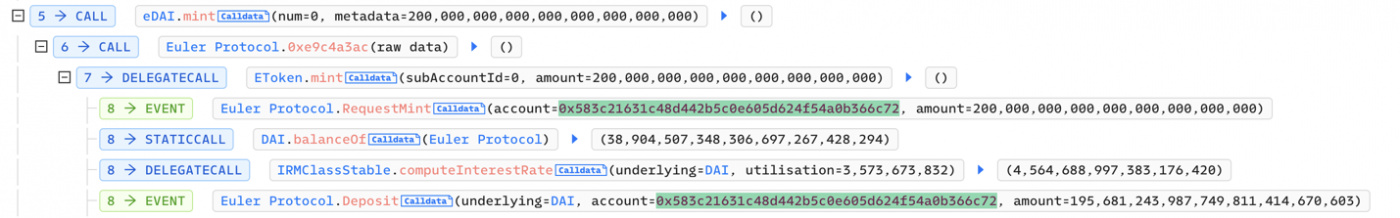
- Attacker creates another 200m leverage via minting ~195.6m eDAI tokens and 200m dDAI tokens.
- Attacker donates 100m eDAI tokens via donateToReserves function and creates undercollateralized position
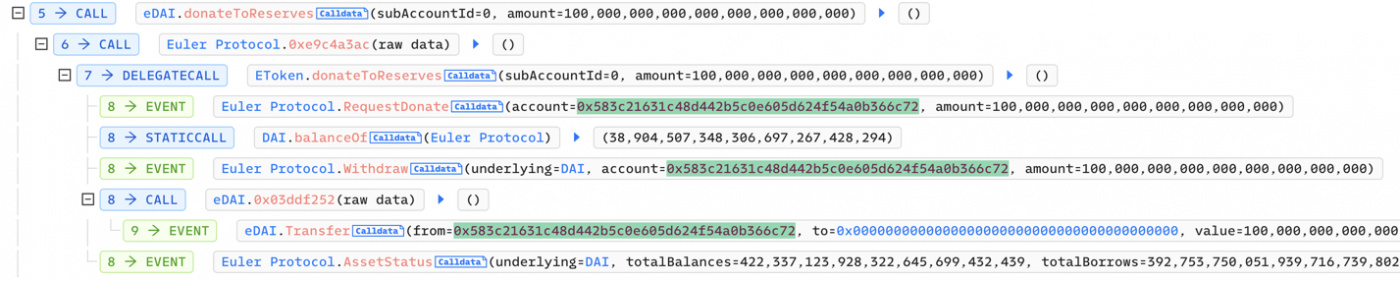
After all actions attacker has the following balances:
~310m eDAI
~390m dDAI
Attacker now has 80m more dDAI tokens than eDAI, which makes his position undercollateralized and it can be exploited via liquidation by another attacker’s account.
Due to the fact mentioned before, system will use current collateral amount of attacker when liquidating. When performing a liquidation of his account attacker will receive full amount of eDAI, but only a part of dDAI, which will be also lowered by discount.
- Attacker liquidates undercollateralized position using another account
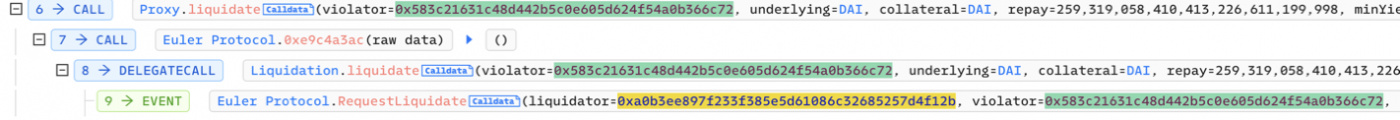
Health level of this position is low, which allows an attacker to gain maximum discount. Coversion rate will be 1.25 eDAI per dDAI, which finally results in attacker gaining 310m eDAI tokens and around 259m dDAI tokens.
Now attacker account which liquidated a position has a good health and can withdraw extra eDAI. Attacker withdraws 38m eDAI and gains around 38.9m DAI.
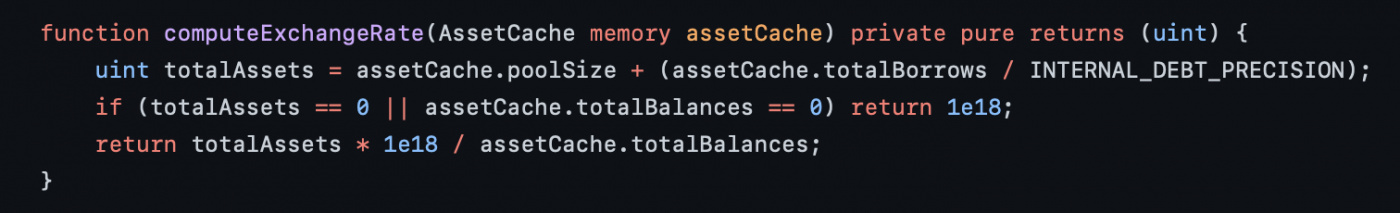
This conversion rate was possible due to the fact that assetCache.totalBorrows was increased during liquidation process because of extra repayment.
A total profit for this transaction was around 8.9m DAI (8.8m USD).
Attacker has also exploited other assets same way which resulted in a total loss of ~197m USD.

